Introduction
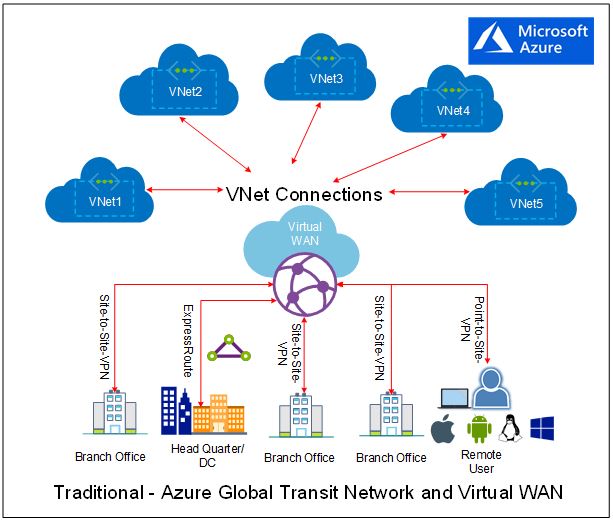
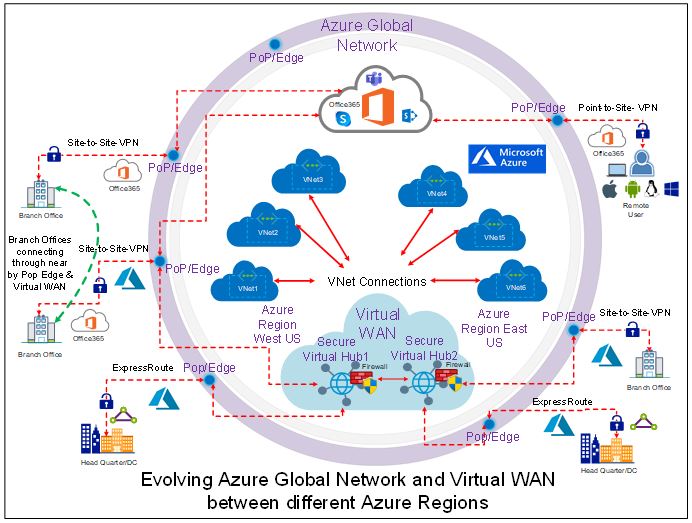
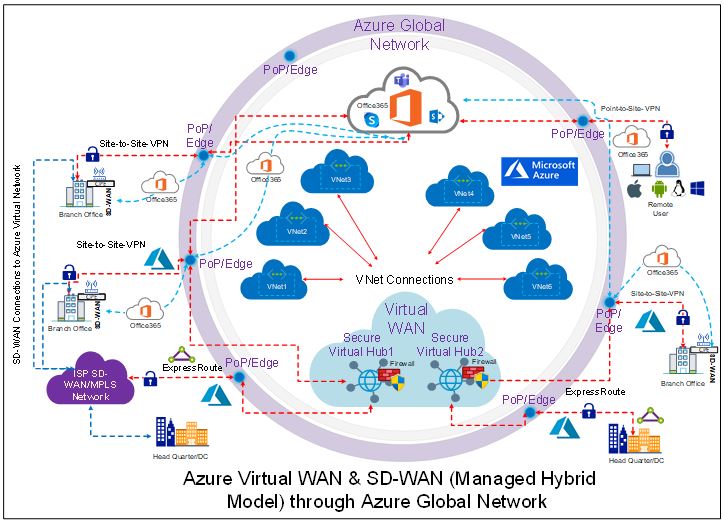
Last month, I have published my below two articles on Azure Virtual WAN and SD-WAN and both describes on how a cloud hosted and migrated application effectively can be accessed by business through an optimized network with a greater performance and with a low latency even from remote sites:
- Co-existence between Azure Virtual WAN and SD-WAN is shifting a gear in the digital transformation
- Microsoft Azure Virtual WAN – How it’s getting closer to Business!
During this discussion, I also touched based on how business can access their cloud hosted application through a nearby available POP/Edge presence and these Edge/POPs are not only available from major cloud service providers such as Microsoft, Amazon and Google but also from a large number of Telcos to align their current and future digital transformation need of edge computing in a 5G network.
In this article, we will discuss on currently how major cloud services providers and telecom operators are jointly working on edge computing services in their 5G network roadmap and then finally will cover the use cases and benefits of Microsoft released edge computing services.
With the rise of 5G network connectivity, there are n numbers of possibilities to deliver immersive, real-time experiences that needs ultra-low latency, and connectivity requirements. 5G sets a new paradigm shift in telecom industry with enhanced mobile broadband up to 10x faster, reliable low-latency communication
Telecom providers partnering with CSP’s for 5G Edge
A large number of telecom operators i.e. AT&T, CenturyLink, Etisalat, NTT Communications, Proximus, Rogers, SK Telecom, Telefónica, Telstra, Vodafone and others have partnered with Microsoft on their effort and plan to make these Azure Edge Zones available to customers for 5G edge networks.
On the other side, SK Telecom, KDDI, Verizon, Vodafone Group and few others operators are also partnered with Amazon Web Services (AWS) to develop its edge computing services through AWS Wavelength on 5G networks. An AWS wavelength will be deployed by its operator partners to provide ability to developers for building applications that serve end-users with single-digit millisecond latencies over the 5G network.
Google is in the same move and partnering with telecom providers such as AT&T, Vodafone and others to harness 5G as a business services platform. To meet this goal, Google Cloud recently announced its Global Mobile Edge Cloud (GMEC) strategy, which will deliver a portfolio and marketplace of 5G solutions built jointly with telecom companies which is an open cloud platform for developing these network-centric applications and a global distributed edge for optimally deploying these solutions.
Google Cloud also announced Anthos for Telecom, which will bring its Anthos cloud platform to the network edge, allowing telecom companies to run their applications wherever it makes the most sense.
Microsoft Edge Computing Services ‘Azure Edge Zones’
In the end of Mar’2020, Microsoft has announced their edge computing services called “Azure Edge Zones” (currently available in preview), which are designed to provide the cloud resources quickly at carrier’s 5G network and enables data processing very close to end user. With this, business developers now can deploy cloud resources such VMs, containers, and other selected Azure services into Edge Zones to address the low latency and high throughput requirements of applications near to their business locations/sites.
Azure has not released just one service but there are three types of edge zones and these referred to as Azure Edge Zones, Azure Edge Zones with Carrier and Azure Private Edge Zones respectively. Each Edge Zones are connected to Azure’s own network and runs in existing Microsoft network POP/Edge locations where Azure CDNs, Azure Front Door’s and other services are running with an appropriate security control.
With Azure edge zones, Microsoft is gearing up towards to an important telecom industry space which blends the cloud computing with mobile networks and making strength of 5G edge computing for enterprises, IoT, and applications which operates on a very low latency.
In simple terminology, an Azure edge zones are local extensions of Azure services to enterprises which are ideal for solving compute, storage, and service availability problems by allowing business to provide experience-driven resources closer to their locations/sites. Azure edge zones are available through Azure (Azure Edge Zones), with select carriers and telecom operators (Azure Edge Zones with carriers), or as private customer zones (Azure Private Edge Zones).
Azure edge zones overall benefits
As per Microsoft, Azure edge zones provides a rich, seamless customer experience in real time with ultra-low-latency edge compute capabilities. Below are the major benefits of Azure edge zones but not limited to:
Solve edge latency problems with 5G network – Accelerate a quick application and virtualized network function (VNF) deployment to provide a seamless compute, storage, IoT, and container services to business. The low edge latency and high bandwidth of Azure edge zones and 5G networks virtually eliminates the latency concern.
Better application performance and data control – Azure edge zones enable faster access to local Azure services to get granular control of data and better performance by deploying apps at the edge and these apps are such as critical industrial IoT and media services workloads. Development of distributed applications across cloud, on-premises, and edge using the same Azure Portal, APIs, development, and security tools.
Deliver better mobile experiences with 5G network – Provide a better real-time experience for businesses and developers by deploying reliable, latency-sensitive applications, high-density graphics gaming’s on wireless networks with “Azure edge zones with carriers”. An acceleration of IoT, artificial intelligence (AI), and real-time analytics by optimizing, building, and innovating for robotics, automation, and mixed reality.
Boost private edge performance with 5G network – Get the lowest latency possible for any industrial use case through a fully automated service-delivery experience with Azure private edge zones.
Extend your on-premises to Azure by using SD-WAN appliances – By using SD-WAN appliance on the same private edge zone appliance, customer can extend their on-premises networks across multiple branches to Azure. SD-WAN provides seamless branch office connectivity that’s orchestrated from redundant central controllers at lower cost of ownership.
Use Case & Scenarios
It becomes important to understand the specific use cases of each types of released Azure edge zones and for that we will talk about all the use cases on each edge zones separately. Azure Edge Zones and Azure Private Edge Zones deliver consistent Azure services, applications platform, and management to the edge with 5G network by unlocking new scenarios.
As per below Microsoft article – https://docs.microsoft.com/en-us/azure/networking/edge-zones-overview, the typical use case & scenarios for edge zones are available as below:
- Real-time command, control in robotics,
- Real-time analytics and inferencing through artificial intelligence & machine learning.
- Machine vision.
- Media streaming and content delivery.
- Surveillance and security.
- Remote rendering for mixed reality and VDI scenarios.
- Immersive multiplayer gaming.
Azure Edge Zones
Common applications include distributed apps and public cloud-based business and consumer platforms in industries like retail, media, financial services so typical use cases of Azure edge zones include as below:
- Gaming and game streaming.
- Media streaming and content delivery.
- Real-time analytics and inferencing via artificial intelligence and machine learning.
- Rendering for mixed reality.
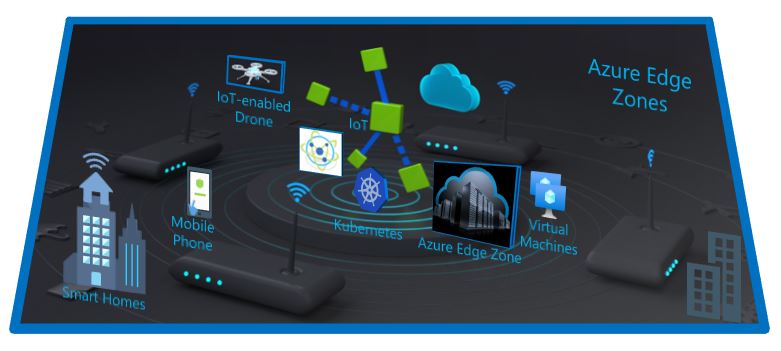
Below figure-1: Azure Edge Zones represents the scenarios of above said use cases by using the Kubernetes, IoT, Azure edge zones services.
Azure Edge Zones with carrier
5G speed and bandwidth makes ingesting, delivering, and processing data faster and ideal for connected vehicles, mobile platforms and interactive games, high-bandwidth video streaming, and other business-critical scenarios.
Typical use cases of Azure edge zones with carrier include all 4 use cases of Azure edge zones plus two more as below:
- Connected automobiles.
- Tele-medicine.
Below figure-2: Azure Edge Zones with Carrier represents the scenarios of above said use cases by using the Kubernetes, IoT, Azure edge zones services, 5G mobile carrier and connected vehicles.

Azure Edge Private Zones
Azure Private edge zones are small-footprint extensions of Azure which are based on the “Azure Stack Edge” platform and are placed on-premises. It enables low latency access to computing and storage services deployed on-premises
With private LTE and 5G speed, high bandwidth, and ultra-lower latency, Azure Private edge zones are ideal for optimizing the performance of connected robotics, big data analytics, mixed reality, and other automation-driven applications.
SD-WAN on Private edge zones also let customer to move from a capex-centric model to a software-as-a-service (SaaS) model to reduce IT budgets.
Private mobile networks enable ultra-low latency, high capacity, and a reliable and secure wireless network that is required for business-critical applications. Private mobile networks enable scenarios such as command and control of automated guided vehicles (AGV) in a warehouse, real-time communication between robots in a smart factory and augmented reality, and virtual reality edge applications.
Typical use cases of Azure edge private zones include as below, all use cases for this service is different except one ‘Real-time analytics and inferencing with AI and ML’.
- Real-time command and control in robotics.
- Real-time analytics and inferencing with artificial intelligence and machine learning.
- Machine vision.
- Remote rendering for mixed reality and VDI scenarios.
- Surveillance and security.
Below figure-3: Azure Private Edge Zones represents the scenarios such as command and control of automated guided vehicles (AGV) in a warehouse, real-time communication between robots in a smart factory (industry robotics), augmented reality and surveillance security.
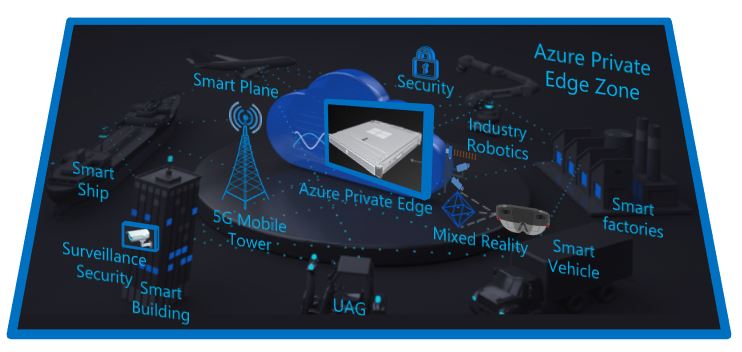
Azure Private edge zone also lets developers to develop and deploy applications on-premises by using the same familiar tools that customer use to build and deploy applications in Azure. Azure also lets customer to below:
- Run private mobile networks (private 5G, private LTE).
- Implement security functions like firewalls from various technology partners such as Affirmed, Mavenir, Metaswitch, Nuage Networks from Nokia, Palo Alto Networks, and VeloCloud from VMware.
- An evolving platform building with customers, carriers, and industry-partners to allow seamless integration and wide selection of Virtual Network Functions (VNFs), including 5G software and SD-WAN
As this Azure Service is new and running under Preview currently, we will have more further use cases and in depth discussion once this service is in ‘general availability’ release.
Rajeev Ujjwal has more than 18 years of transformation delivery experience in cloud computing, infrastructure, directory service, and cyber security with larger global customers. He is a senior cloud consultant and successfully delivered various kind of global project delivery such as greenfield, consolidation, separation and migration.